We have implemented technological solutions that are now operating successfully in real business environments. Each case reflects how the right configuration and adoption generate tangible value and sustainable results. These projects have been developed together with our partners, aligning technology, strategy, and operations. The result: proven solutions that drive efficiency, continuity, and growth in organizations.
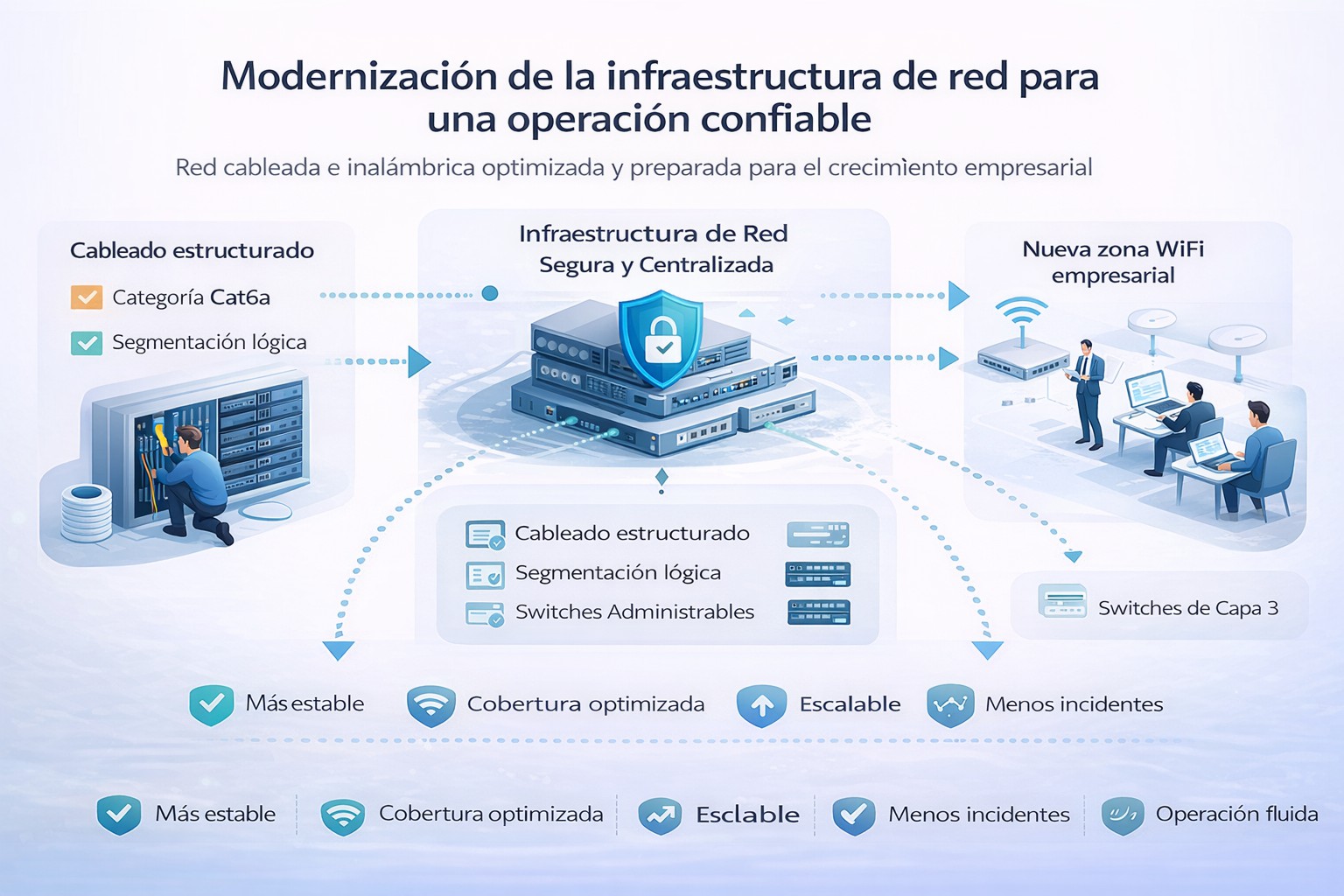
The organization faced limitations in its network infrastructure that affected stability, performance, and growth capacity. It needed a reliable and secure network that could support critical business operations, improve connectivity, and be prepared for future technological demands.
Gen3sis designed and implemented a comprehensive wired and wireless network infrastructure, modernizing structured cabling, reorganizing the physical layer, and deploying a centrally managed enterprise WiFi network. The solution incorporated logical segmentation to optimize traffic, improve security, and ensure a consistent connectivity experience across all areas of the organization.
This approach enabled us to build an orderly, scalable network aligned with the real needs of the business, without any interruptions during operation.
This solution reflects how, under the Industry 5.0 approach, infrastructure is no longer just technology but becomes an enabler of people’s work and business continuity.
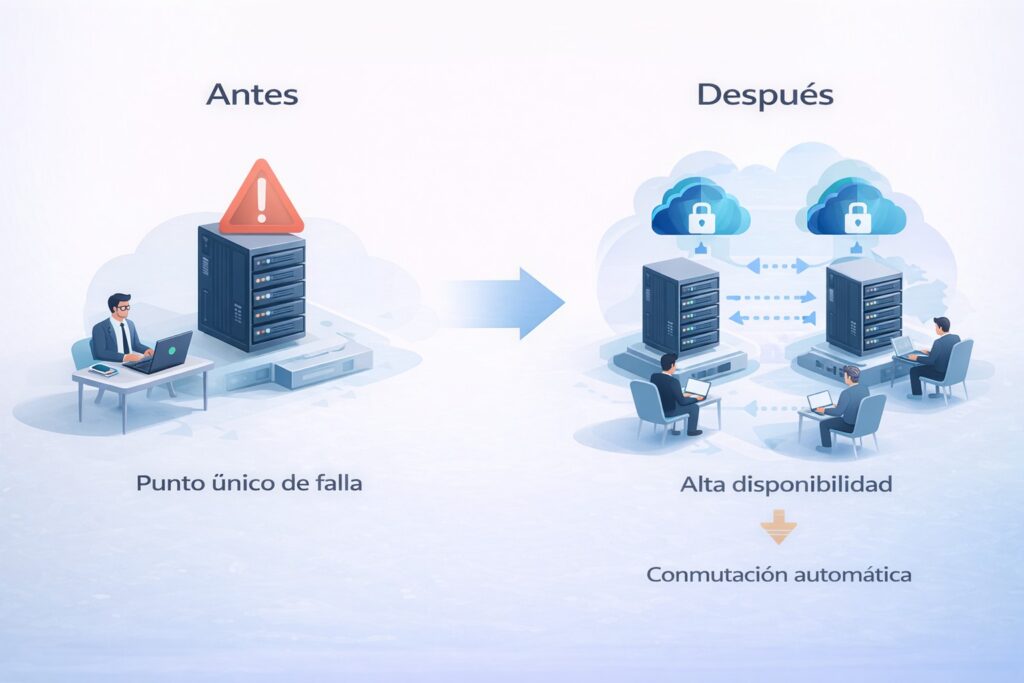
Gen3sis designed a high-availability architecture based on virtualization, distributed across two geographically separate sites that are securely connected. The solution incorporated service replication, failover automation, and technical validations to ensure data integrity.
Thanks to this architecture, in the event of any incident in the main environment, services are automatically restored without manual intervention and without impact on users.
This case demonstrates how, under the Industry 5.0 approach, technology becomes a silent enabler that protects operations, supports people, and ensures business continuity.
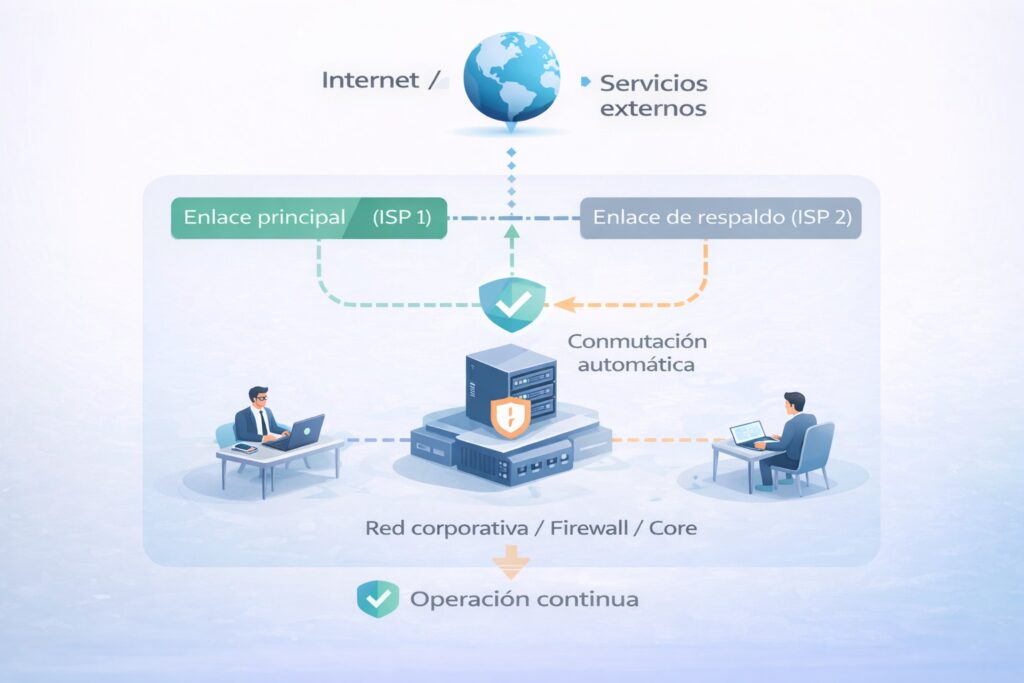
The customer’s operations depended on a single internet connection. Any failure by the primary provider meant service interruptions, lost productivity, and operational risks. The challenge was to ensure continuity of connectivity without complexity for users or the IT team.
Gen3sis implemented a connectivity redundancy scheme, incorporating a second internet connection and configuring automatic switching policies that allow traffic to be redirected transparently in the event of any failure.
The solution was designed to operate intelligently, prioritizing service stability and ensuring that users maintained access to systems and applications without experiencing any interruptions.
This case demonstrates how a simple but strategic architecture, aligned with the Industry 5.0 approach, protects operations and allows people to continue working without friction.
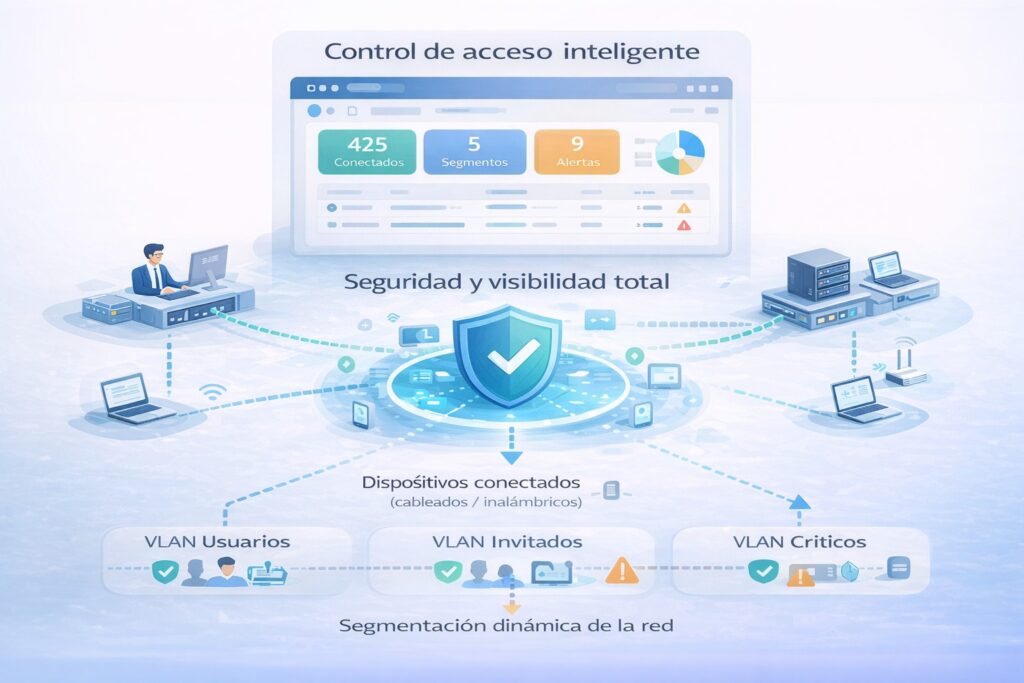
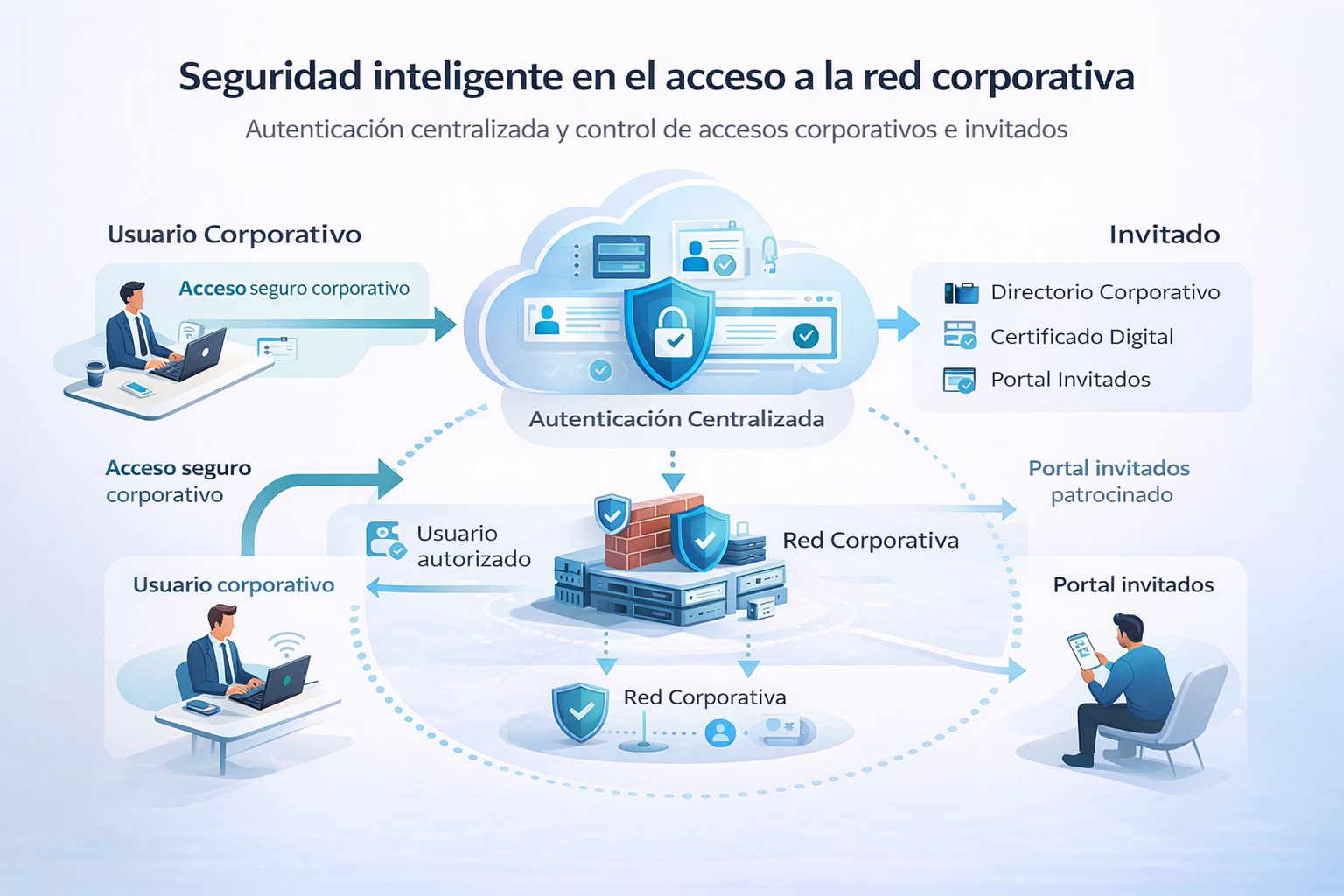
Gen3sis carried out a process of optimization and fine-tuning of the access control platform, enabling its full operation. Dynamic policies, automatic network segmentation, device posture control, and complete visibility of the wired and wireless environment were configured.
The solution enabled each device and user to be evaluated in real time, applying intelligent access rules aligned with the organization’s security policies.
This case shows how, under the Industry 5.0 approach, security ceases to be an obstacle and becomes an intelligent enabler that protects operations and supports people in their daily work.
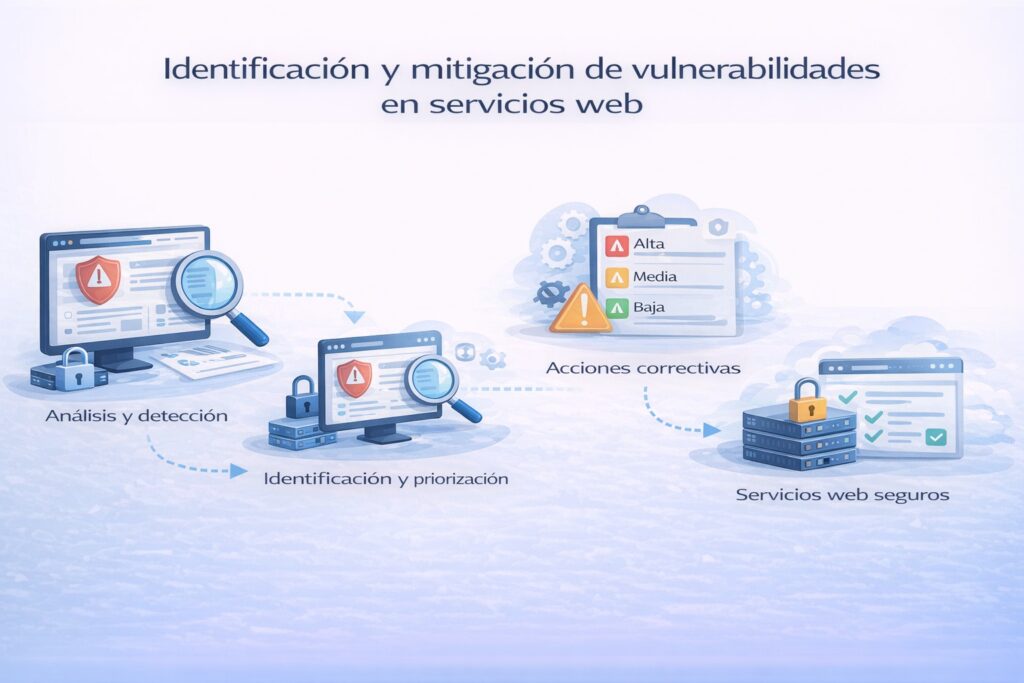
The organization needed to know the actual level of exposure of its external web applications and services. Faced with an environment increasingly exposed to threats, it was essential to identify vulnerabilities before they could be exploited, reducing risks to information, operations, and the business’s reputation.
Gen3sis performed a vulnerability analysis using a white box approach, evaluating applications and systems from a thorough and controlled perspective. Through specialized tools and expert technical analysis, weaknesses affecting the confidentiality, integrity, and availability of information were identified.
The process included not only detection, but also risk prioritization and the delivery of clear, actionable recommendations, facilitating decision-making and effective mitigation.